Ransomware protection is an essential aspect of modern cybersecurity strategies, especially as cybercriminals become increasingly sophisticated. Recent studies indicate that many businesses underestimate the threat posed by ransomware, often relying solely on endpoint protection solutions that may not provide sufficient defense. The alarming statistic that one-third of organizations experienced a ransomware attack in just the past year underscores the need for comprehensive security training for employees. Phishing emails remain the primary vehicle for delivering ransomware, emphasizing the vital role that user education plays in preventing breaches. By integrating robust security measures with effective training, businesses can significantly enhance their resilience against potential ransomware attacks.
Ensuring robust defenses against malicious software, particularly ransomware, is critical for organizations facing today’s daunting digital threats. With the evolving landscape of cyber risks, the failure of common endpoint defenses highlights the urgency for improved protective measures. Vulnerabilities often arise from users falling victim to deceptive phishing emails, making proper training a cornerstone of preventative strategies. By fostering awareness and readiness among employees, companies can create an invisible barrier against cyber threats, effectively minimizing the odds of a successful security breach. Embracing a holistic approach to digital safety not only strengthens technical defenses but also empowers personnel as the first line of defense against ransomware.
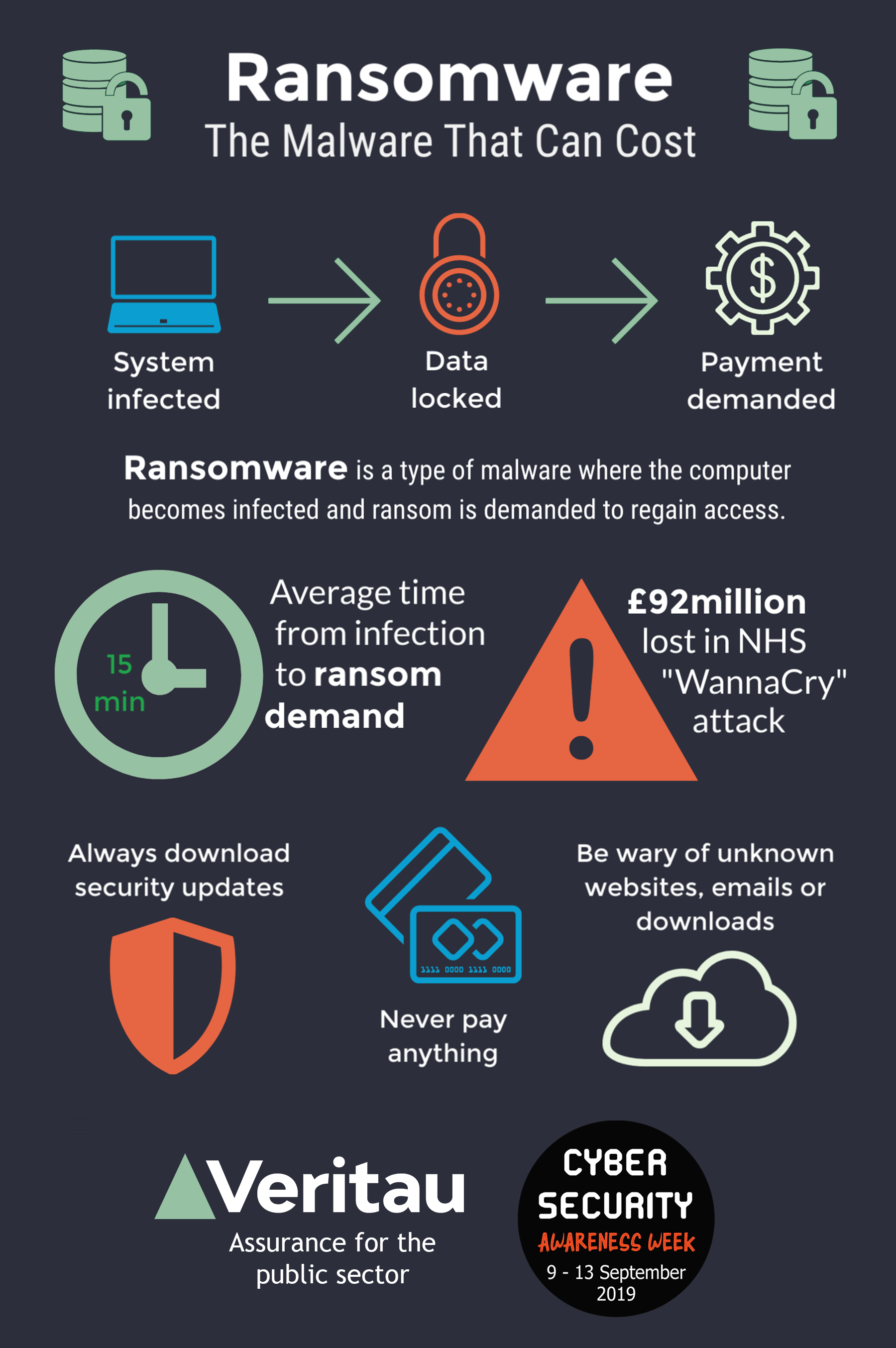
Understanding the Threat of Ransomware
Ransomware has rapidly become the most profitable venture for cybercriminals, as evidenced by the disturbing rise in attacks. Recent statistics reveal that one in three organizations have fallen prey to ransomware within the last year, highlighting the urgent need for effective protective measures. The alarming fact that even companies employing multiple security solutions still succumbed to breaches underscores the inadequacy of traditional endpoint protection. This indicates a pressing need for organizations to re-evaluate and bolster their cybersecurity strategies to counteract the evolving nature of ransomware.
The consequences of a successful ransomware attack extend far beyond immediate financial losses, affecting productivity and operational efficiency. With an average of six endpoints and two servers breached during an attack, the disruption can result in significant downtime for businesses. On average, victims reported nearly 24 hours of combined downtime from users and IT responses. This emphasizes the importance of understanding ransomware not just as a singular event but as a widespread threat that can cripple multiple aspects of an organization.
The Role of Security Training in Ransomware Protection
One of the most critical factors in thwarting ransomware attacks lies within the organization itself—its employees. As stated by cybersecurity expert Stu Sjouwerman, the primary delivery method for ransomware is via phishing emails. This underscores the necessity for comprehensive security training that equips employees to recognize and respond appropriately to potential threats. By fostering a culture of cybersecurity awareness, companies can develop a ‘human firewall,’ drastically reducing the likelihood of successful attacks.
Effective security training programs not only educate employees about the dangers of phishing but also empower them to act as the first line of defense against cyber threats. Employees trained to question unexpected emails and to follow security protocols can significantly alter the risk landscape. As organizations integrate regular training sessions and simulated phishing tests, they foster a proactive approach to cybersecurity, which is essential for enhancing their ransomware protection strategies.
Why Endpoint Protection Alone Isn’t Enough Against Ransomware Attacks? (with SEO focus on Endpoint Protection)
When it comes to safeguarding against ransomware, relying solely on traditional endpoint protection methods is proving ineffective. Despite the installation of advanced antivirus software, many organizations find themselves vulnerable due to a lack of comprehensive measures. Studies show that over half of organizations deploying multiple antivirus solutions still experienced ransomware breaches, highlighting a critical gap in protective strategies.
To properly defend against ransomware, organizations need to implement a multi-layered security approach that incorporates not only endpoint protection but also continuous monitoring, threat intelligence, and employee training. Combining technology with robust security training creates a formidable defense, ensuring that if one barrier fails, others remain in place. Investing in advanced endpoint protection solutions that utilize machine learning and behavioral analysis can further enhance the organization’s capabilities, arming them in the battle against cybercrime.
Comprehensive Strategies for Ransomware Prevention
To effectively prevent ransomware attacks, organizations must adopt a comprehensive approach that incorporates technology, processes, and training. Ransomware threats are complex and ever-evolving, necessitating a robust strategy that goes beyond basic defenses. Implementing a combination of reliable security tools, such as firewalls, endpoint protection platforms, and real-time monitoring systems can create a solid foundation for cybersecurity.
Moreover, organizations are encouraged to continuously update their systems and software to guard against newly discovered vulnerabilities that could be exploited by ransomware. Routine security assessments can help identify weaknesses, enabling teams to strengthen their defenses proactively. By combining these layers, companies significantly reduce their risk of falling victim to cyberattacks and enhance their overall resilience.
The Financial Impact of Ransomware Attacks
Beyond operational disruption, the financial ramifications of ransomware attacks can be staggering. Many organizations face tough decisions regarding whether to pay ransoms, with reports indicating that those who do can expect to pay between three and five bitcoins for data decryption. The average cost can range between $3,780 to $6,300—an amount that can cripple small businesses and significantly impact larger enterprises within the context of overall budgets.
Despite the temptation to pay ransoms for expedience, a significant majority of businesses choose to refrain, seeking alternative recovery methods instead. With 94% of surveyed organizations opting not to pay, it’s crucial to develop thorough preparedness plans that prioritize data backups, recovery strategies, and business continuity measures. This proactive stance not only minimizes financial loss but also fortifies overall cybersecurity efforts.
Implementing a Strong Cybersecurity Framework
Establishing a strong cybersecurity framework is vital for safeguarding against ransomware and other cyber threats. A solid cybersecurity posture blends technology, processes, and people, fostering a culture of security awareness throughout the organization. By adopting frameworks such as the NIST Cybersecurity Framework, organizations can create structured approaches that align their cybersecurity efforts with overall business objectives.
Key components of this framework include identifying assets, assessing vulnerabilities, implementing protective measures, and continuously monitoring for threats. Organizations should prioritize security training as part of their framework to ensure that all employees understand their roles in maintaining security. This holistic approach to cybersecurity not only protects against ransomware but also strengthens an organization’s resilience against a myriad of cyber threats.
The Importance of Continuous Monitoring in Cybersecurity
Continuous monitoring plays a critical role in a comprehensive cybersecurity strategy, particularly in detecting and responding to ransomware threats. By implementing real-time surveillance systems, organizations can quickly identify abnormal behaviors indicative of potential attacks. Proactive monitoring of network traffic and endpoint activities allows for immediate action to be taken before an attack escalates.
Furthermore, continuous monitoring aids in compliance with data protection regulations by ensuring that security practices are consistently maintained. Organizations can correlate data from various sources, revealing insights that can inform overall security policies and procedures. This level of vigilance is essential in today’s digital landscape, where cyber threats are constantly evolving.
Building a Robust Incident Response Plan
Developing a robust incident response plan is essential for organizations to respond effectively to ransomware attacks. This plan should outline clear steps to take in the event of a breach, including communication protocols, resource allocation, and steps for recovery. A well-defined response strategy minimizes confusion and facilitates quick recovery when an attack occurs.
Additionally, conducting regular drills and simulations helps employees familiarize themselves with the process, ensuring everyone knows their roles during an incident. An organization can significantly reduce downtime and the overall impact of an attack by preparing employees and IT teams to act swiftly and efficiently. Continuous evaluation and updating of the incident response plan in light of new threats can further enhance resilience.
The Need for Comprehensive Cybersecurity Policies
Comprehensive cybersecurity policies serve as the foundation for protecting organizations against ransomware and other cyber threats. These policies encompass guidelines for data protection, employee conduct, and incident response, helping to create a security-conscious culture. Establishing clear policies ensures that all employees understand their responsibilities regarding cybersecurity, thereby reducing the likelihood of human error, which is often the root cause of security breaches.
Regularly reviewing and updating these policies is essential to address emerging threats and incorporate new best practices. Policies must also ensure compliance with relevant legal and regulatory requirements, safeguarding the organization from potential penalties. By prioritizing comprehensive cybersecurity policies, organizations can create a strong defense against the ever-changing landscape of cybersecurity threats.
The Future of Cybersecurity: Trends and Innovations
As ransomware continues to evolve, so too must the strategies and technologies we employ to combat it. Future trends in cybersecurity are likely to focus on more advanced technologies, such as artificial intelligence (AI) and machine learning, to enhance detection and response capabilities. These innovations can automate many aspects of cybersecurity, enabling organizations to quickly respond to threats and mitigate potential damage.
Additionally, the rise of remote work has changed the cybersecurity landscape, requiring new protocols and protections. Organizations must adapt to these changes, ensuring that all endpoints—whether in the office or remote—are secured. This adaptability will be paramount in developing a forward-thinking cybersecurity posture capable of addressing the challenges of tomorrow.
Frequently Asked Questions
What is ransomware protection and why is it important in cybersecurity?
Ransomware protection refers to measures taken to guard against malicious software that encrypts data and demands payment for decryption. It’s crucial in cybersecurity because ransomware attacks can cripple organizations, leading to significant downtime, financial loss, and data breaches. Understanding how to enhance ransomware protection is essential for any organization’s security strategy.
How can endpoint protection enhance ransomware protection?
Endpoint protection enhances ransomware protection by providing security measures that shield devices from malware infections, including ransomware. It includes software that detects and isolates threats, preventing ransomware attacks from infecting endpoints. However, relying solely on endpoint protection may not be sufficient; combining it with user training and awareness programs improves overall effectiveness.
What role does cybersecurity training play in ransomware protection?
Cybersecurity training is vital for ransomware protection as it equips employees with the knowledge to recognize phishing emails and other threats that often deliver ransomware. By fostering awareness, organizations build a ‘human firewall’ capable of preventing infections, thereby significantly enhancing their ransomware defense.
How do phishing emails contribute to ransomware attacks?
Phishing emails are a primary vector for ransomware attacks. Cybercriminals use deceptive messages to trick users into clicking harmful links or opening malicious attachments that deploy ransomware. Effective ransomware protection involves training users to identify and avoid phishing attempts, significantly reducing the risk of infection.
What are common signs of a ransomware attack that organizations should be aware of?
Common signs of a ransomware attack include sudden file encryption, inaccessible files, ransom notes demanding payment, and unusual network activity. Organizations should have robust ransomware protection strategies in place that enable quick detection and response to these indicators.
What strategies can organizations implement to improve their ransomware protection?
Organizations can improve ransomware protection by employing a multi-layered security approach. This includes effective endpoint protection, regular software updates, strong password policies, and rigorous security training for employees to recognize phishing attempts. Additionally, having a backup strategy ensures data recovery without paying ransom.
What should an organization do if it has been a victim of a ransomware attack?
If an organization falls victim to a ransomware attack, it should immediately isolate affected systems to prevent further spread. Next, they should assess the damage, notify law enforcement, and, if possible, restore data from backups. It’s also crucial to analyze how the breach occurred to improve future ransomware protection efforts and bolster cybersecurity measures.
Are there specific tools recommended for ransomware protection against evolving threats?
Yes, various tools can bolster ransomware protection such as advanced endpoint protection software that includes behavior analysis, ransomware-specific detection, and remediation capabilities. Additionally, security awareness solutions that simulate phishing attacks help train users to identify and respond appropriately to threats.
| Key Point | Details |
|---|---|
| Ransomware Threat | Ransomware is a major business model for cybercrime, affecting numerous organizations. |
| Detection Challenges | 53% of organizations using multiple protection solutions were still victims of ransomware. |
| User Education | Training users to recognize phishing attempts is crucial as ransomware is primarily delivered through email. |
| Impact of Attacks | On average, six endpoints and two servers are affected in a single ransomware attack, leading to significant downtime. |
| Ransom Payments | 94% of businesses surveyed did not pay the ransom, and those who did paid between 3 to 5 bitcoins. |
Summary
Ransomware protection is essential in today’s digital landscape as attacks grow more sophisticated. Organizations must prioritize user education to recognize phishing emails, which are the primary delivery method for ransomware. The findings suggest that traditional endpoint protection solutions may not be enough, indicating a need for a robust security strategy that includes training employees to create a ‘human firewall.’ By adopting this approach, businesses can enhance their overall security posture and mitigate the risks associated with ransomware.